Arlo SAML 2.0 Authentication
SAML 2.0 is an open standard for authentication and authorization. Arlo supports login to the management platform, customer portal and customer checkout.
This is an example of what your login page can look like after setting up your preferred login methods:
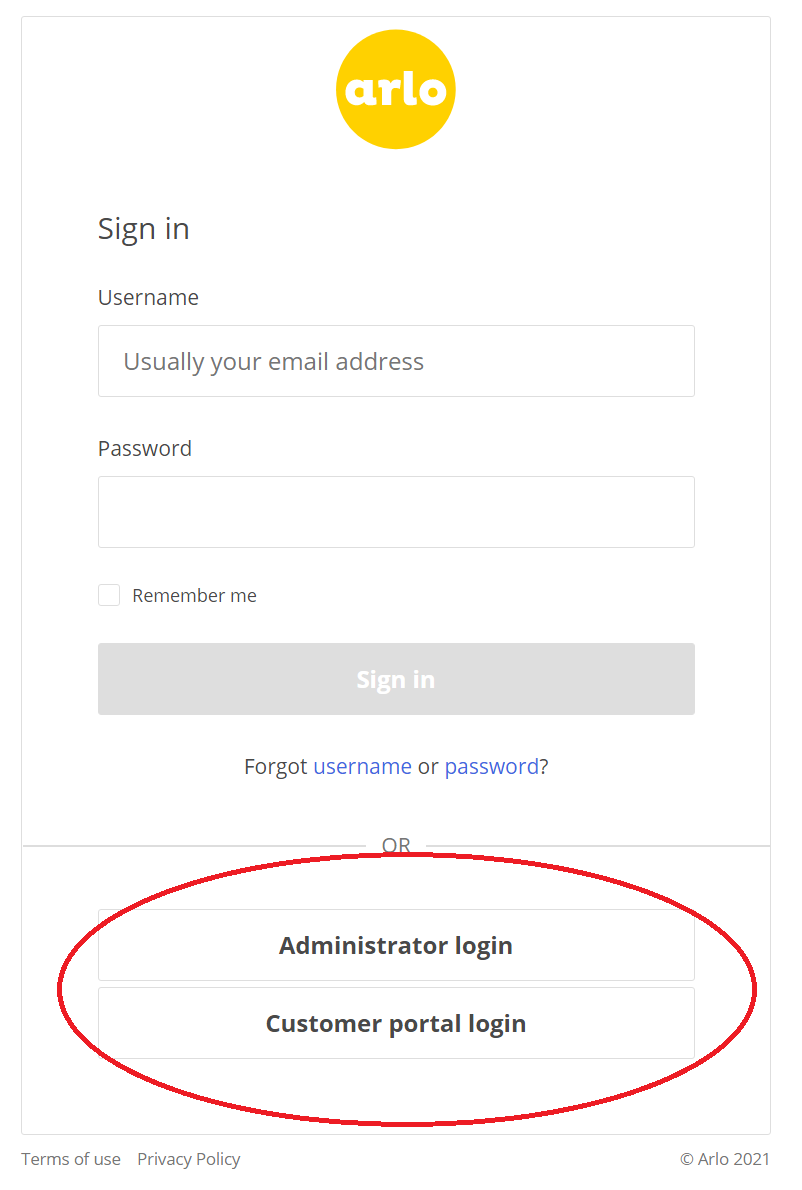
Text on each button is fully customizable.
Terminology
Identity provider (IDP) - The system that issues authentication for a user
Service provider (SP) - Arlo is the SP in our case. The SP accepts identities provided by the IDP
Just-in time (JIT) provisioning - Creating a user account in Arlo "just in time" as they're required
Metadata - Each IDP and SP provides a public XML metadata document with information about the system. By convention accessible at saml2/metadata
Getting started
All configuration can be accessed via https://{yourplatform}/management/Console/#/settings/saml/
You may wish to deploy a trial platform to use as a sandbox to confirm your configuration works with Arlo as intended.
Setup
You can create new IDP records directly on the settings page. Make sure you create the right one for your desired purpose:
Pick New management IDP if the IDP is to be used by your administrators or managers logging into the management platform or your presenters logging into the Arlo for Mobile app.
Pick New customer portal IDP if the IDP is to be used by your customers in the checkout or when logging into the customer portal.
After you create your IDP record in Arlo, download the metadata file by clicking the Download Arlo metadata button. That saves your metadata file in xml format on your computer. (The file extension does not say ".xml", but you can safely add that should your IDP setup require it). You should use this file directly to setup a new IDP endpoint - it contains data about Arlo required by the IDP for everything to work properly.
You can edit each IDPs settings by selecting the desired IDP in the Identity providers section dropdown, then pressing the Edit button to the right. Only IDPs that are enabled in the setting show up on the login page, giving you full control over which of the IDPs you've set up are visible to your customers. If you wish to remove some of your unused IDPs, please contact Arlo support.
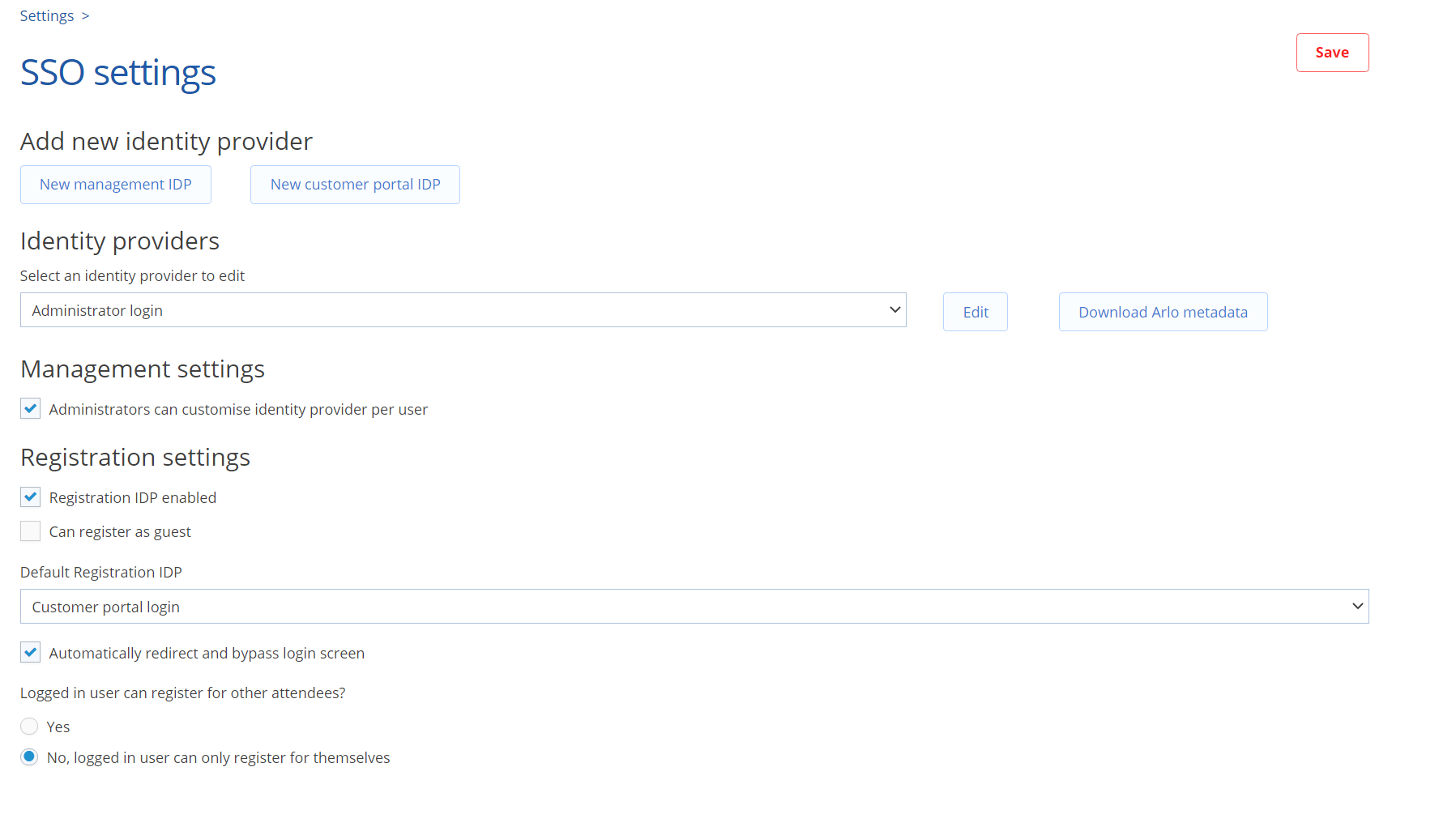
Configuration options
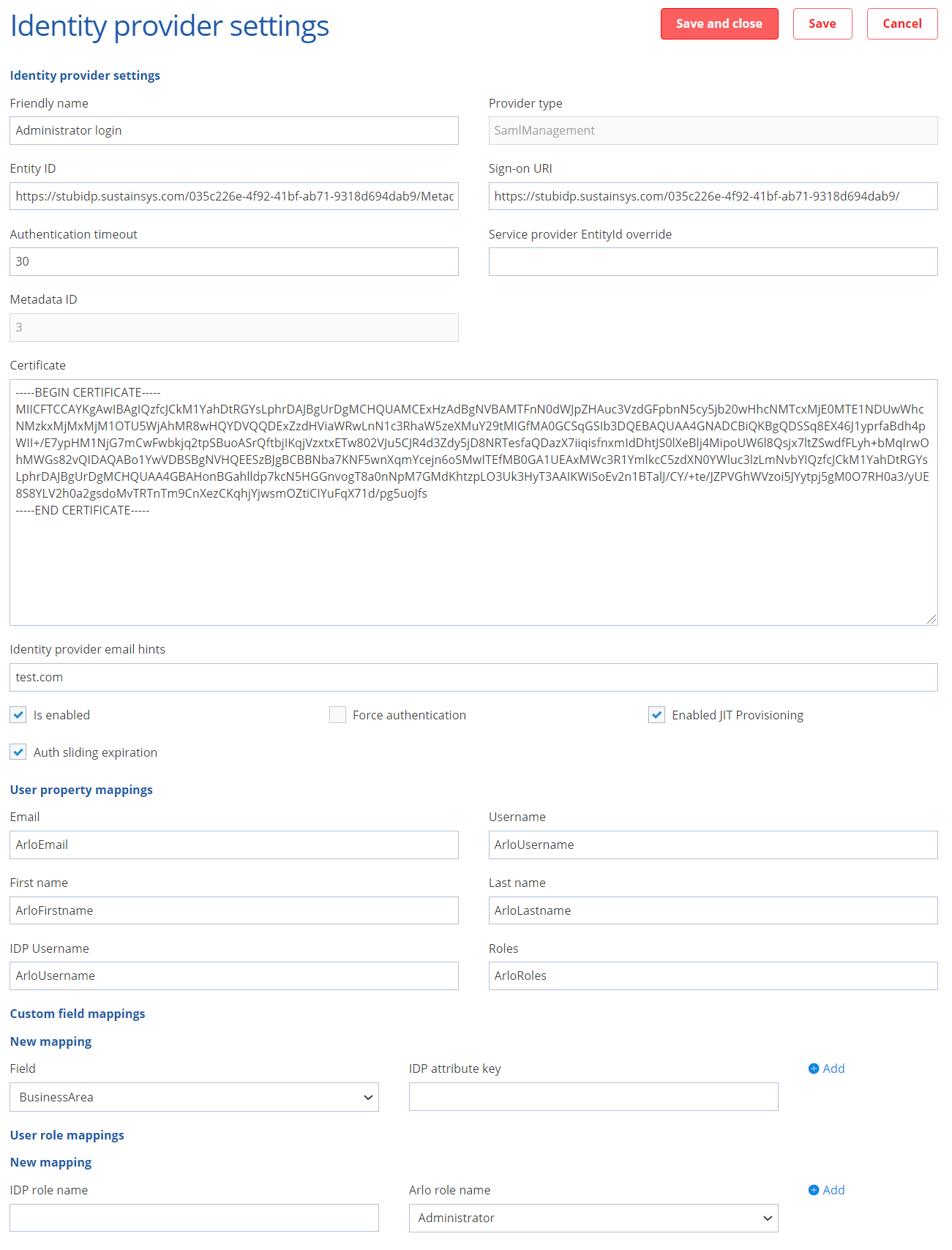
The key fields in the IDP settings are Entity ID, Sign-on URL and Certificate. These can be found in the metadata file provided by your IDP. Ensure these are fully formatted, this tool will ensure your certificate is in the right format to upload.
Name / Friendly name: Text that directly appears on the button on the login page
Entity ID: EntityID. Can be found in IDP metadata
SignOnUri: The login page URI of the IDP. Can be found in IDP metadata as property SingleSignOnService (redirect binding)
Authentication timeout: Sets the time in minutes for how long you are authenticated within Arlo using this IDP. 30 minutes is suitable for Customer portal / checkout IDP, we recommend at least 90 minutes for administrators.
Service provider EntityID override: (optional) overrides the SP EntityID. By default it will be the platform URL
Certificate: Certificate provided in IDP metadata
IDP email hints: Outdated field which can be safely ignored. We are working on removing it.
Is enabled: Enables this IDP to be used, shows it as a button to be used on your login page.
Force authentication: Tell the IDP that you must re-login every time you authenticate over SAML. Some IDPs may not support this attribute. We don't recommend this option for Customer portal / checkout, because the user is interrupted in his experience if he is already logged in with the IDP.
Enable JIT Provisioning: If enabled accounts will be created on the fly in Arlo as users login for the first time. If not the user must be pre-created in Arlo and mapped to a user in the IDP
User property mappings: Dictionary of attribute names provided by the IDP and the associated user fields they should be mapped onto in Arlo. These map to the metadata fields provided by your IDP and have to be set up properly for the SSO option to work. Contact Arlo support with the metadata file generated by your IDP handy if you have issues configuring your IDP.
User role mappings (Management only): Relates to your "Roles" mapped field. It maps values in the role field specified to Arlo roles - Administrator, Business Manager (read-only role) or a Presenter.
Testing your setup
Once you have set up your IDP configuration and enabled the IDP, you can start testing via either the login portal or checkout. You can enable and set the registration (checkout) Identity Provider.
Management platform / Customer portal
Once the IDP is enabled, the login portal shows you a button you can click to log in using the IDP. It's recommended you test this in UAT first or at a time of low traffic.
Checkout / Website
Warning: In a live system this will affect all users trying to access your checkout. It's recommended you test this in UAT first or at a time of low traffic.
In the Registration settings section of the SSO settings page, tick the Registration IDP enabled checkbox and select your IDP from the Default Registration IDP dropdown.
Provisioning / migrating users to new IDP
Depending on whether you use JIT provisioning or not you will have different experiences. Please contact Arlo support if you have a large volume of users who exist already and you would like them to be migrated to an IDP login method.
JIT provisioning
In this mode any user that logs in will be created on the fly.
If an administrator or a presenter is created this way, it assigns them a license if available and that user is set to use the provisioning IDP as a log in method.
If there is a user with the same first name/last name/username/email already, the user can't be created this way.
If it is the same user, an administrator can change the log in method for the user on the contact page in the security tab, so that the user can use the IDP login next time around.
Manual provisioning (JIT disabled)
This is the recommended approach for your management platform users. This requires a manual step by an administrator before a user logs in. The username field is a unique field which is also used to store unique user ids from the IDP. You must manually set the IDP of an existing user in Arlo to that of the desired IDP and match their usernames with the one provided by the IDP to ensure they are the same user.
Popular Identity Providers:
Arlo SAML authentication has been tested against popular IDP's. See below links for further information on integration:
